Original content provided by BDO Australia.
The strongest cyber security is only as good as its weakest link. This includes your supply chain. As an organisational leader, you need to be cognisant that clients or partner organisations may not have the strong defences your organisation has in place. If they have succumbed to a phishing or other cyber attack, their weaknesses may become yours.
What happens when a business email account is compromised?
Let’s talk about what might happen should a scenario of BEC with one of your business partners or clients becomes a reality.
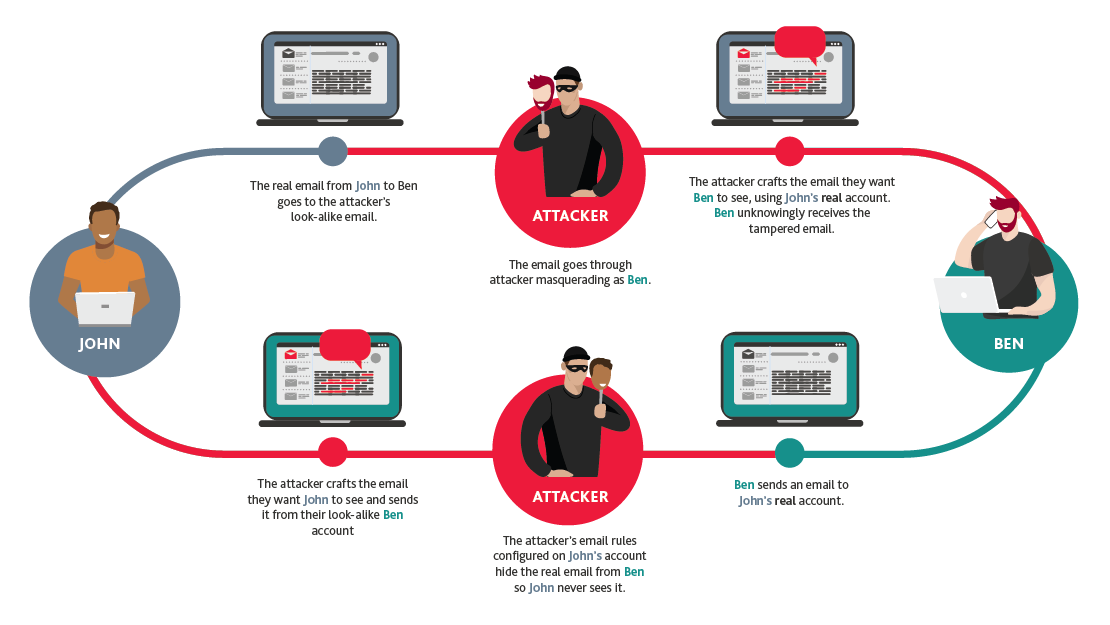
- When a client or partner organisation’s email account is compromised, the emails you receive will be from their legitimate email address, so there will be no red flags for your information security defences to detect.
- Contrary to popular belief, not all threat actors create emails full of typos and bad grammar or commence with “Dear Customer”, meaning employees, who are arguably one of your best lines of defence, may not detect anything out of the ordinary.
- By responding to the ‘legitimate’ email address, you effectively provide the attacker with control of the chain of communication.
- Once the email chain is subverted, the attacker, masquerading as your business partner or client, takes control of all email correspondence between the two parties. This means the attacker will see all correspondence and only allow the genuinely intended recipient to see select emails and those the attacker has altered or crafted.
- This process allows the attacker to conduct business with you as usual (masquerading as your business partner or client), and this is when the malicious intent manifests itself. The attacker can search for, and access, financial and other sensitive information and hide messages and responses they don’t want the user to see.
- Once ingrained, the attacker can alter your invoices or provide an update to your vendors’ bank account details to redirect funds to their own accounts.
- The compromise is often only discovered when the intended recipient does not receive their payment (or payments) and makes enquiries via another contact person or direct phone call and the masquerade is exposed. In some cases, this could be months after the initial compromise.
While processes and procedures can be put in place to help mitigate this type of attack, we still see successful fraudulent transactions like this occur far too often.
The BEC process
In addition to financial losses, the impact BECs may have on your organisation includes:
- An increase in cyber insurance costs
- Compromised trust in your organisation
- Inflict reputational damage
- Potential theft of sensitive and personally identifiable information
- A potential regulatory compliance requirement (Notifiable Data Breach).
How do I protect a business email account?
As prevention is better than cure, BDO’s Forensic Services team suggests your organisation employs risk prevention processes including:
- Having effective policies and procedures in place when there is a change in client or vendor financial details. Don’t rely on a single contact method to facilitate a change
- Embedding a standard practice to independently verify any financial related requests
- Ensuring your Information Technology (IT) support actively monitors and responds to alerts such as Microsoft Office 365 ‘risky sign-on’ reports, particularly impossible travel alerts
- Regularly auditing the mailbox rules set by your employees
- Critically considering system requirements, such as Outlook Web Access
- Educating and training staff – The human firewall is a critical line of defence
- Enabling O365 audit logging for all users. This will be of tremendous value when things go wrong.
Subscribe to receive the latest BDO News and Insights
Please fill out the following form to access the download.